In the previous blog post, I explained some basics about maximal extractable value (MEV), Ethereum transactions, and the mempool. In that post, you learned how miners could manipulate transactions. In this blog post, I'll walk you through three different types of front running attacks.
It is not the best time to talk about 🦠 viruses. But I can't find a more coherent picture to explain how I can explain bad MEV in the form of front running (Not all forms of MEV are necessarily malicious!) for most readers. So bear with me until someone else suggests another way to describe it. 🤷🏻
Imagine your body is continuously under attack by viruses and bacteria. Ok, you don't have to imagine, it is happening! Don't panic and freak out. If you are in healthy shape, your immune system can handle this. However, if the number of attacks increases and the balance shifts, you most probably get sick.
An open, permissionless blockchain like Ethereum has to overcome hacks and attacks. We have seen exploits and smart contract bugs since the Ethereum hard fork in 2016. Battle hardening is an essential part of open systems to become more and more resilient over time. In my opinion, we must have these kinds of unintended consequences. Otherwise, improvements, innovations, and "evolution" aren't progressing impactfully in the entire crypto space.
Nonetheless, crypto front runners are another side of the story. Bad actors are incentivized to act selfishly and are not good for the ecosystem. They extract value from Ethereum users and people are losing money 💸. A crypto parasite that is harming Ethereum?
Let’s have a look at three front running attacks so I can address one key question in this post for you.
How are front runners attacking Ethereum and its users from the inside?
💹 The Arbitrage Attack
Arb… what? It wasn't a bank or a financial advisor but the crypto industry which made me look up the term. "Ar-bi-trage" – every time I read it 🤯.
Do you know what I mean?
Arbitrage is a riskless profit. As a simple example, it can be the price difference of the same asset between two different crypto exchanges.
Let's say we have two exchanges. We call them the Argyus and Valorum exchange. Both have a JABBA token listed with a JABBA/ETH pair. Argyus offers a JABBA token for 0.1 ETH and Valorum for a price of 0.08 ETH. If you could buy 1 JABBA on Valorum and sell it on Argyus as quickly as possible, you would make 0.02 ETH. That's the arbitrage. You can get the arbitrage by manually or automatically trading. It is well known that trading bots exist.Not a bad thing and not illegal!
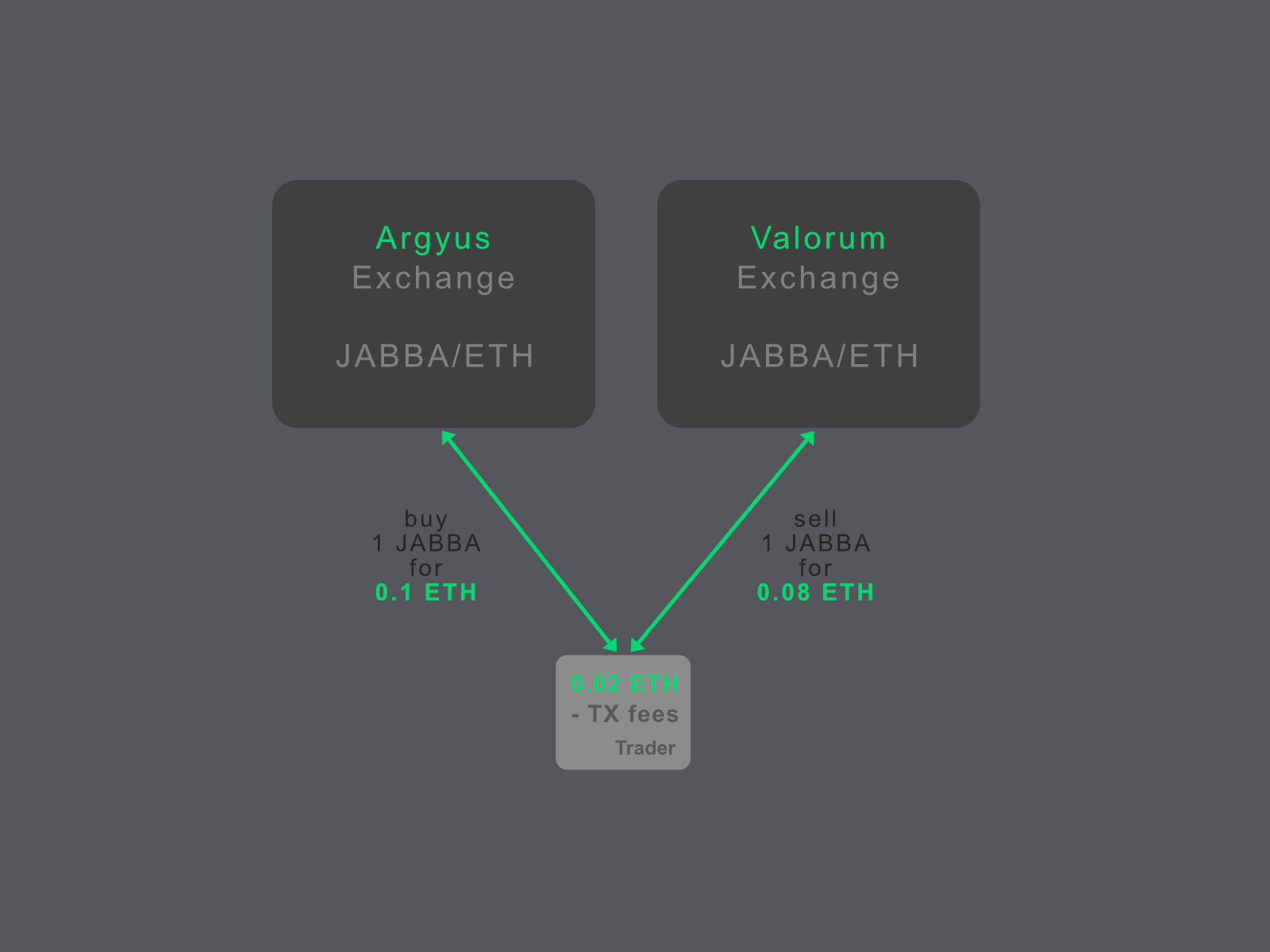
However, in case of an arbitrage attack, it's not you who gets the profit but a bad actor. This bad actor is a front runner. A front runner observes transactions in the mempool and picks transactions with a high arbitrage. He copies your transaction, replaces the recipient address, increases his gas price, and gets his transaction executed with higher priority. If the front runner is also a miner, he can execute the transaction right away. He could also bribe another miner to do the work. If he is confident enough, he waits without additional intervention. Due to the higher gas bid, miners will include their transactions earlier in the block. He receives the reward, and your transaction fails!
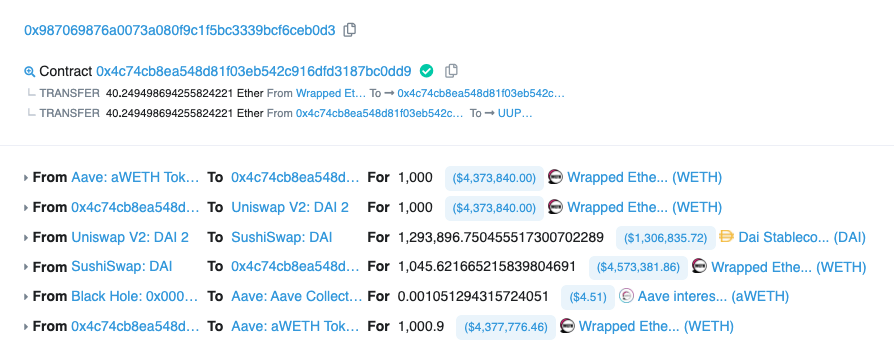
In the following transaction example, you can see an arbitrage trade that turns 1,000 ETH into 1,045 ETH.
🥪 The Sandwich Attack
Sandwiches are yummy. With tomatoes, salad, sliced pickles, cheese and a good piece of ham! But in this attack, the sandwich has a sour taste. 😭
In this attack, your transaction is the topping and gets squeezed by two sandwich toast slice transactions. What does this mean?
Let’s take the decentralized Valorum exchange as an example again. You would like to swap 1 ETH for some $JABBA tokens. You proceed and get 1000 $JABBA tokens and pay some gas fee. Good job! Meanwhile, somewhere else… The attacker also did a good job. He made from your transaction +100 $JABBA tokens. You think that’s totally fine. The market has also done an excellent job! The supply and demand economic game, why should you argue? Here is the reason why you should care. You got squeezed!
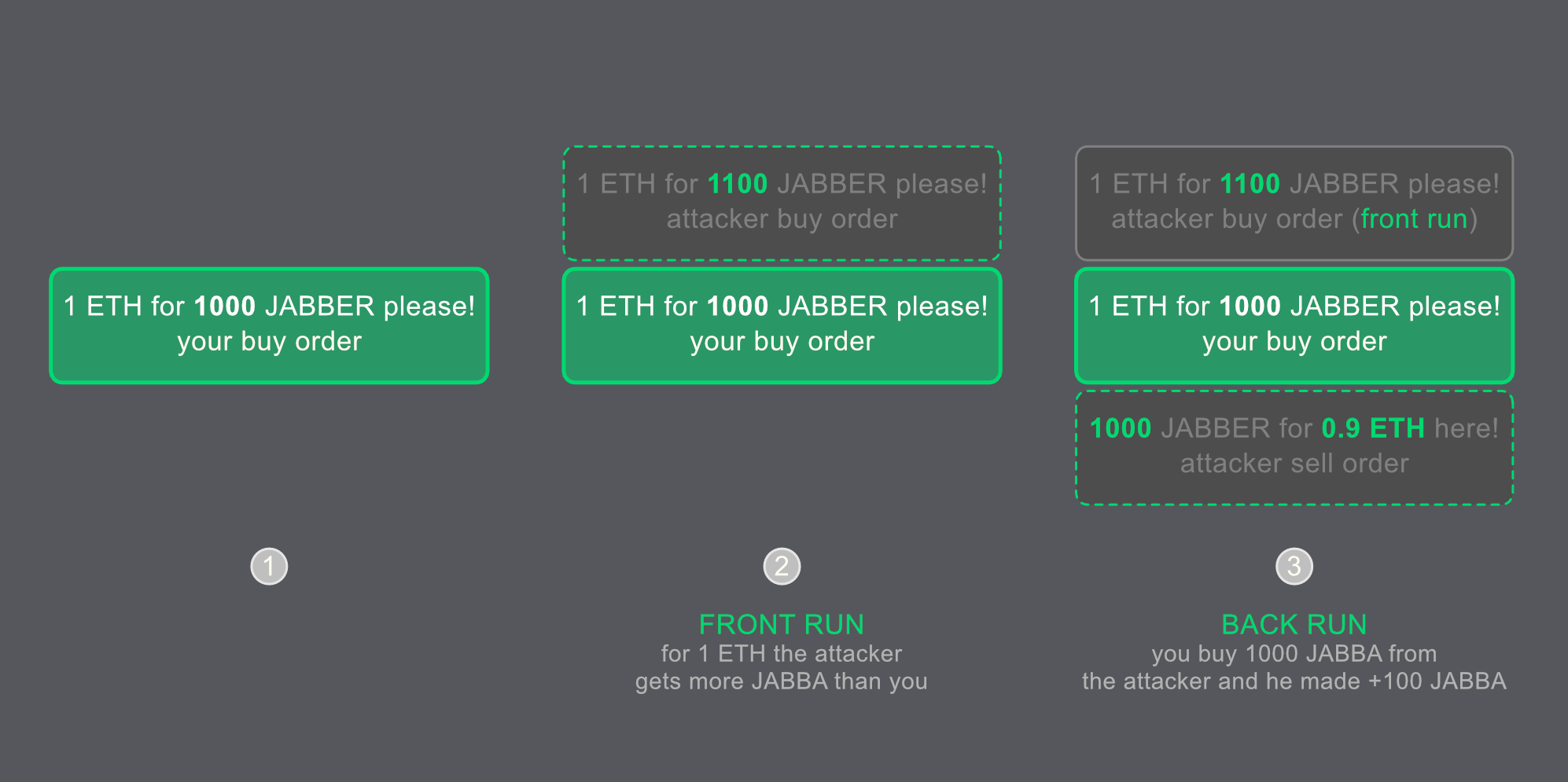
The attacker runs a bot that watches your transaction in the Ethereum mempool. The bot knows that the token price will increase with your JABBA buy order and sends a transaction that front runs your transaction. The attacker's transaction also buys $JABBA tokens for LESS (or more tokens for the same amount of ETH). Right after your transaction, the bot sends a second transaction (gosh, he back-runs you, too!!!) and sells the JABBA token again for a HIGHER (sells less amount of JABBER tokens and gains the difference) price.
🦹🏻♂️ The Time-Bandit Attack
An excellent name for an attack! Can someone steal time like Justin Timberlake? In a time-bandit attack, something similar is happening. In the movie, a time bandit can kill you with a handshake. In the crypto world, a bandit rewrites the history in a chain of blocks. This way, the bandit can reverse transactions and change the state of Ethereum!
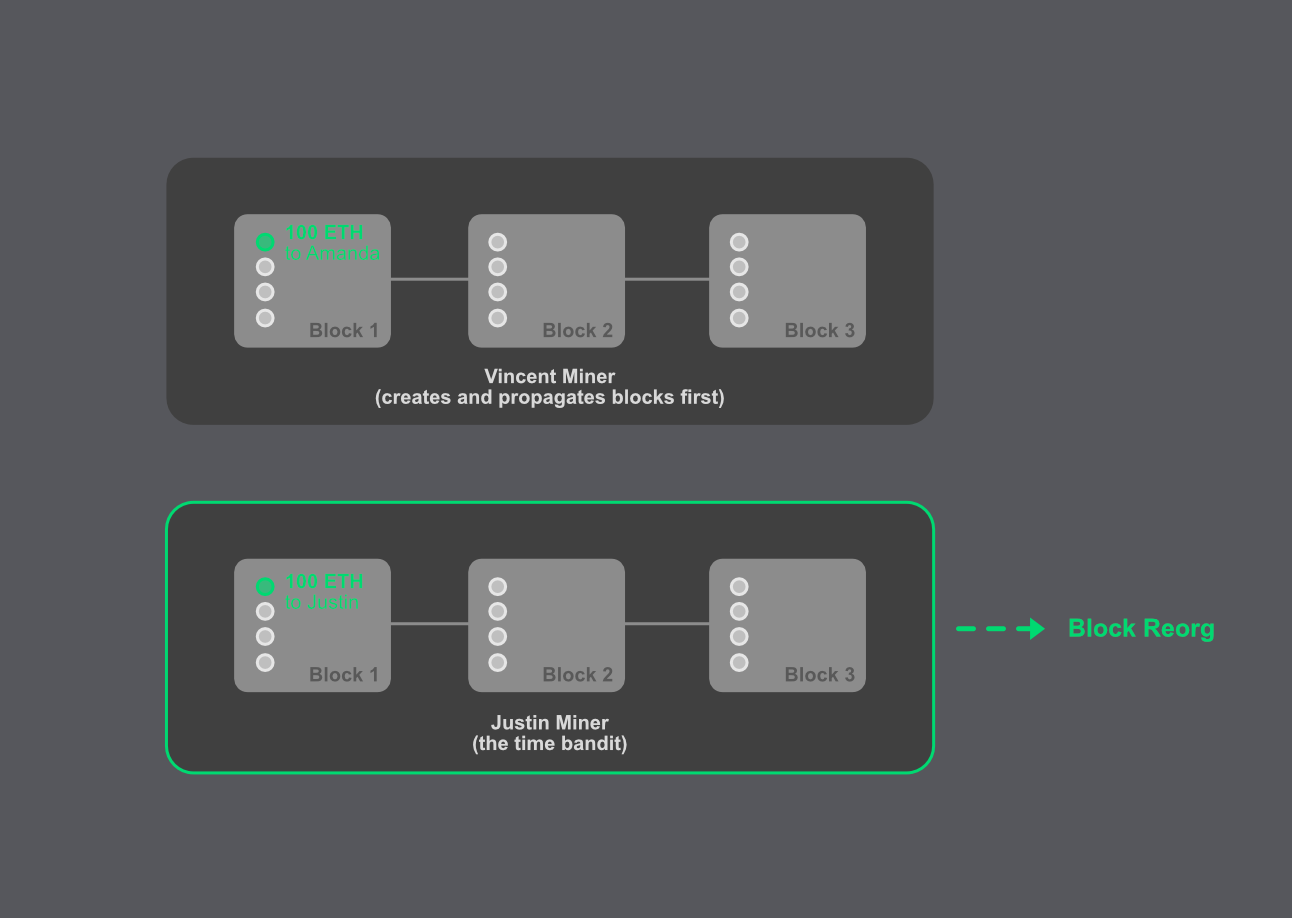
Let's imagine Vincent, a miner, has created the last three blocks and propagated those to the entire network. Justin, the time bandit, saw a shiny 100 ETH of a decentralized exchange (DEX) arbitrage which should go to Amanda. Vincent and Justin are usually happy with the block rewards, but this time Justin puts on his greedy bandit mask and wants to catch the 100 ETH for himself. He re-mines block one to three and changes the one transaction for his favour. Because of the "longest chain rule," the blocks are reorganized to favour Justin's manipulated transaction. Justin rewrote history!
Time travelling is theoretically possible but for the time being it is just fiction. However, for time-bandit attacks, they are possible but still very hard to achieve. In case you want to take the jump into the rabbit hole, check out the in-depth article from Dragonfly Research and learn why time-bandit attacks are very difficult, but once achieved, the attacker could extract a large amount of MEV.
With this post, you have a clearer understanding of how front runner attacks work. It also shows how important it is that the Ethereum community has to find solutions to prevent these attacks that harm end users!
Stay Tuned for More Educational Content
You think, "We are in the blockchain world, and transactions are immutable!?" Yes, they are, but only if sealed in a block! More to come in the next post when I write about block reorgs! Stay tuned! I'll explain how manipulated transactions can be processed in one of the next blog posts.
Is the content helpful for you to understand the MEV problem? I would be happy if you shared it via Twitter to help other crypto newcomers to learn and explore the MEV problem! 🙏
This blog post is a part of Shutters' educational content series. Read it to understand the miner/maximal extractable value (MEV) problem and its impact. Have you missed our previous posts? Browse our blog for more!
Be sure to subscribe to our blog and follow us on X-Twitter for more updates!








