We are excited to introduce the Shutter Explorer, a public interface created to provide insights into the Shutter protocol's operations. This new tool enables users, validators, and developers to access essential data, such as validator activity, transaction lifecycle tracking, and real-time protection against Maximal Extractable Value (MEV) attacks and (real-time) censorship.
As the Explorer is still new and under development, we are eager to receive feedback from the community. Your insights and suggestions are invaluable in refining and improving the Explorer over time. Join us at the Shutter Discord and let us know what you think and how we can improve your experience using this tool!
The Shutterized Gnosis Chain is built on the principles of decentralization, security, and transparency. With the encrypted mempool, the new Explorer, and more, Gnosis Chain has become a blueprint for other L1s and L2s to work towards.
As the Shutter ecosystem expands, it becomes crucial to have clear and accessible tools that offer real-time insight into network operations. The Explorer is a tool for viewing data and understanding how Shutter's innovative encryption technology works. By making this data readily available, the Explorer empowers the Shutter community with transparency and operational visibility. This fosters an open ecosystem where users can engage with and trust the underlying technology.
To learn more about the latest update on the Shutterized Gnosis Chain, check out this post on the Gnosis Blog.
How the Explorer Benefits the Shutter Community
The Shutter Explorer is crucial for reinforcing the values established by the Shutter Network community and Shutterized Gnosis Chain—transparency, accessibility, and decentralization.
Here's how it benefits the community:
Real-Time Transparency
The Shutter Explorer provides real-time insights into the Shutterized Gnosis Chain, offering immediate access to vital information that users can use to make informed decisions.
Enhanced User Experience
We have created the Shutter Explorer with a user-friendly interface, making encrypted transaction data easily accessible to all users. It is valuable for developers and validators, offering both a simplified view of network operations and in-depth technical analysis. The Explorer provides clear insights into Shutter's transaction protection on the Gnosis Chain.
A Comprehensive View: Key Features of the Shutter Explorer
The Shutter Explorer features a comprehensive view of the Shutterized Gnosis Chain's health and performance. Each feature has been carefully crafted to offer clarity and insight into the network's operations.
System Overview
At its core, the Shutter Explorer provides a System Overview that offers a snapshot of the network's health. This overview presents essential metrics related to validators, Keypers, and transactions, enabling users to grasp the network status at a glance.
Here are some of the key metrics you can find on the Shutter Explorer.
- Validator statistics are crucial for the Explorer, as they provide information about the number of validators in the network and their role in verifying transactions and maintaining the integrity of the blockchain.
- The Keyper Overview provides insights into a crucial aspect of the Shutter protocol: the Keypers. Users can see the total number of active Keypers within the Explorer and the threshold required for the network to operate securely.
- The Transaction Overview provides essential information about the total number of transactions on the Gnosis Chain. It tracks the success rates of these transactions and offers historical data on encrypted transactions over time.
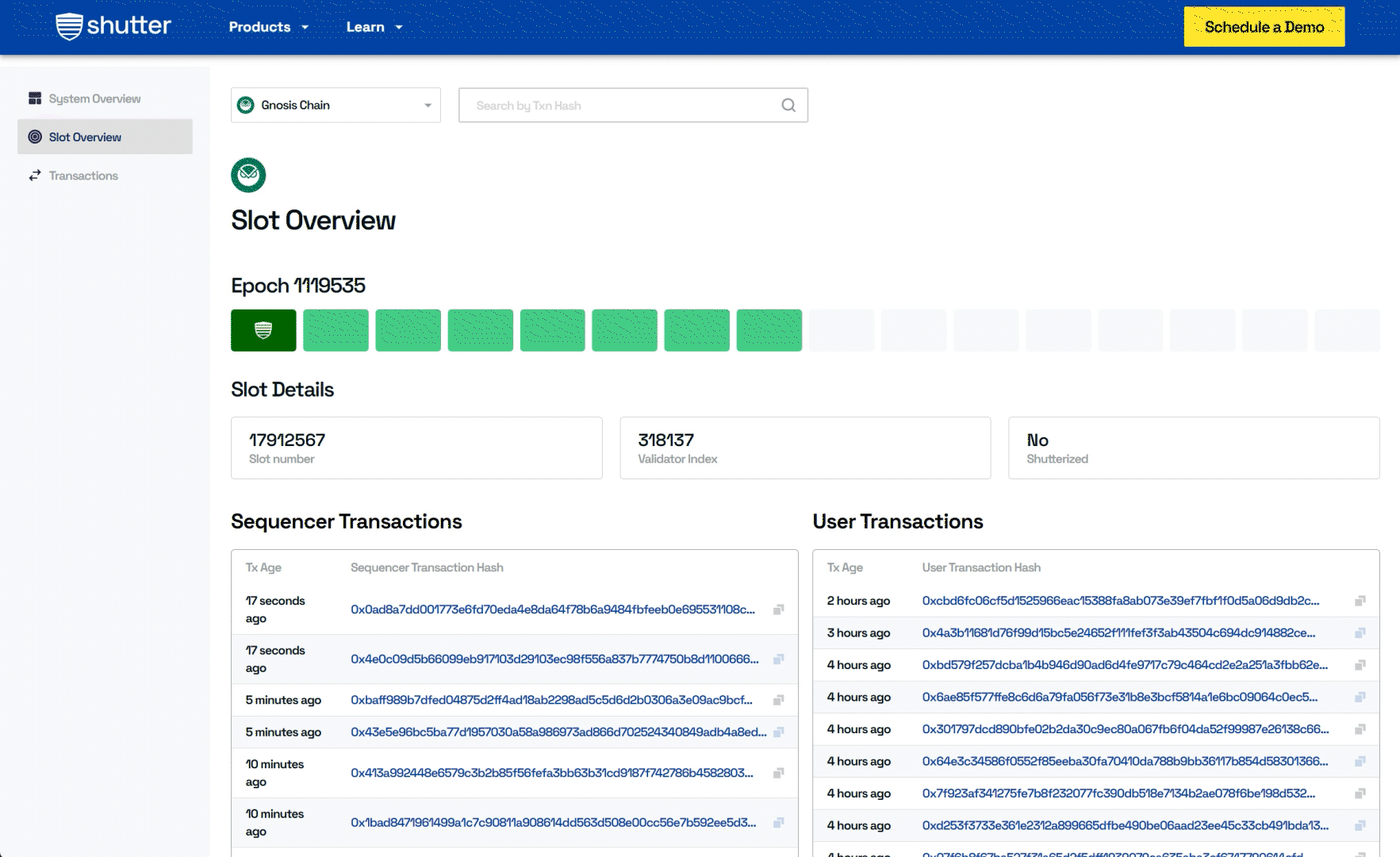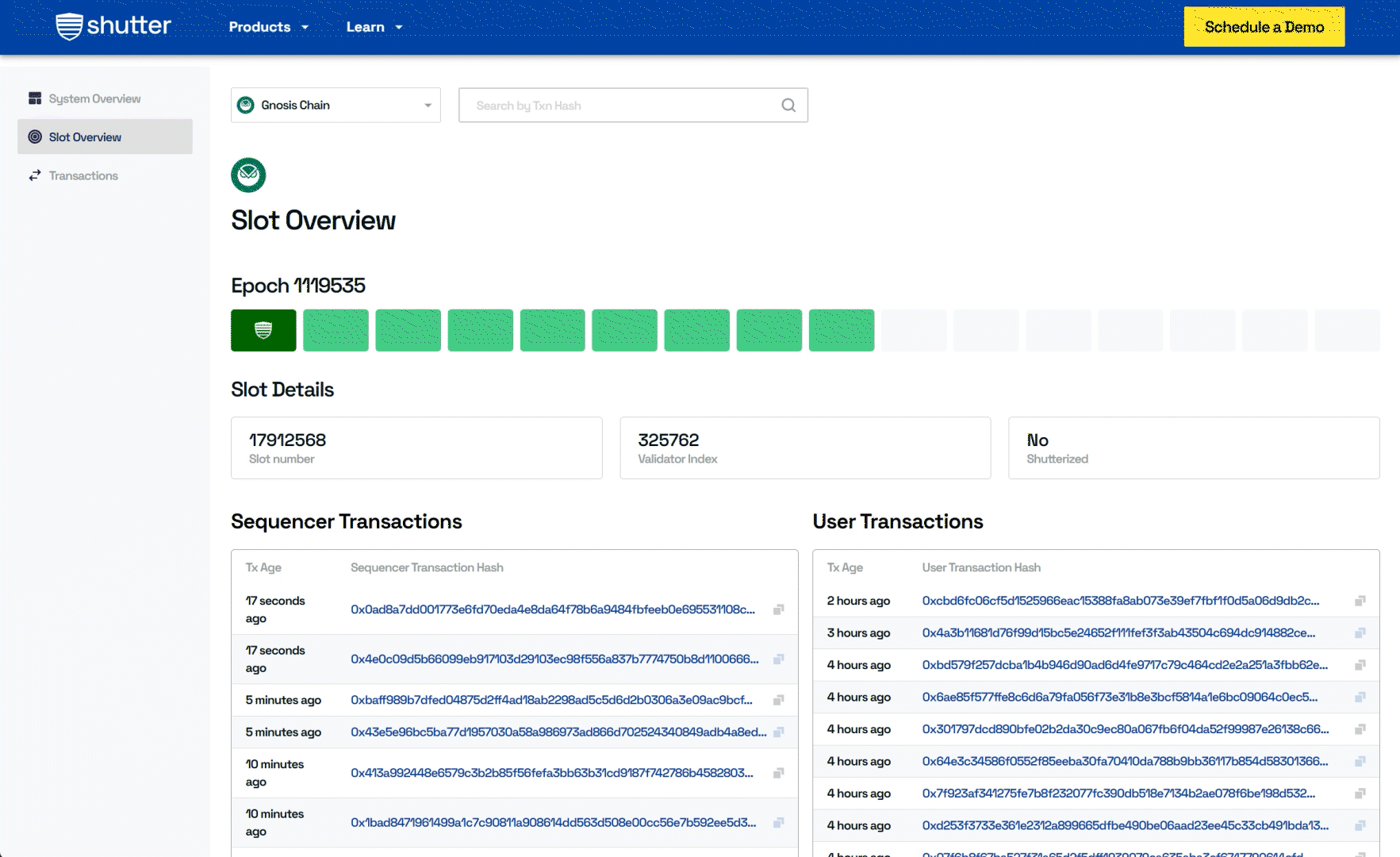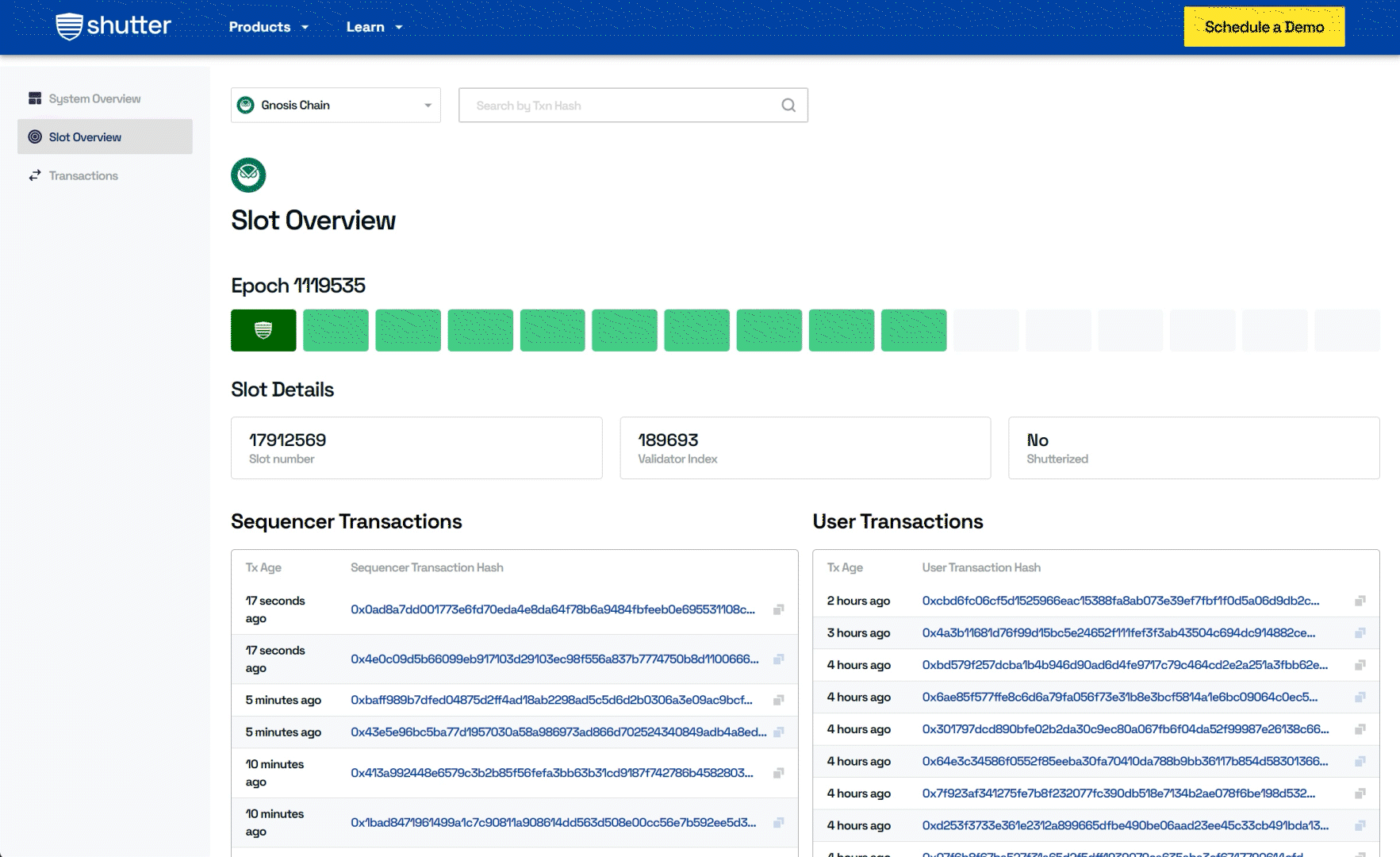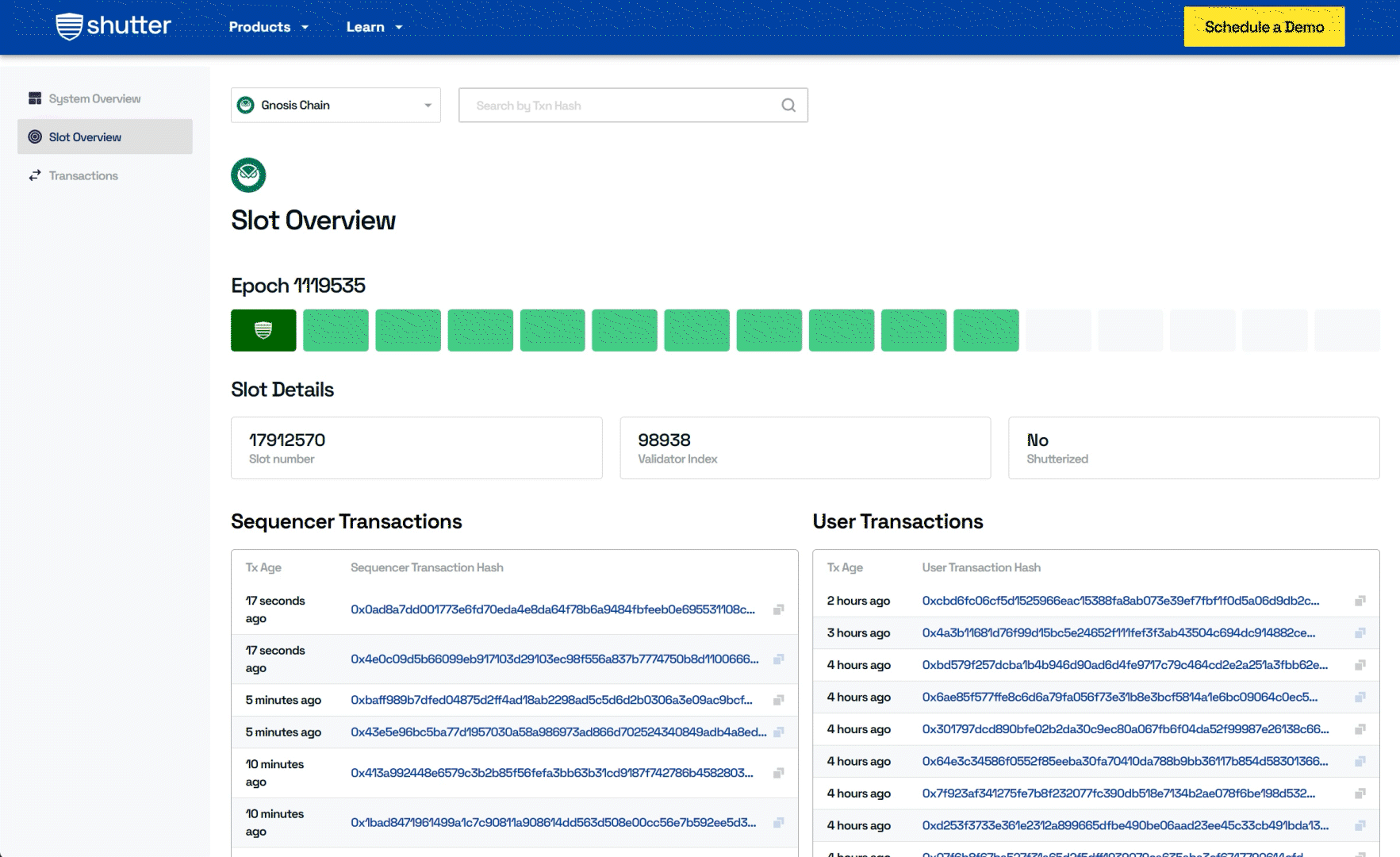
Tracking Key Generation and Slot Progression
Another essential feature of the Shutter Explorer is its ability to provide insights into key generation and slot progression. These are foundational elements of how Shutter operates, particularly regarding the encryption and decryption of transactions.
- Slot Overview: The current epoch and the progression of slots within the Gnosis Chain are visualized, with highlighted shutterized slots for easy identification of encrypted transactions.
- Decryption Key Overview: This section offers a comprehensive overview of the decryption process, providing users with insight into how Shutter's encryption functions to secure transactions in real-time.
In-Depth Transaction Details
The Transaction Detail page offers a comprehensive view for users who want to analyze individual transactions.
- Search Functionality: The Explorer allows users to search for specific transactions using either the transaction hash or the encrypted transaction hash.
- Transaction Lifecycle: Each transaction's entire process is clearly defined step by step, starting from when it is submitted to when it is placed in the encrypted mempool, to the release of the decryption key, and finally, its inclusion in a block.
- Pending and Included Transactions: Users can also monitor both pending and included transactions, ensuring they have complete visibility into what is happening in the network at all times.
How to Use the Transaction Lookup on Shutter Explorer
When you send an encrypted transaction using Shutter, it remains encrypted and won’t appear on GnosisScan until it is processed. To help you track your transaction status while it’s still shielded, we created the Transaction Lookup tool on Shutter Explorer.
Steps to Use the Transaction Lookup
After submitting your transaction (e.g., via MetaMask), remember to copy your transaction hash (Tx ID).
Paste in Shutter Explorer: Go to the Transaction Lookup section of Shutter Explorer and paste your transaction hash into the input field.
View the Status
The tool will show one of the following statuses:
- Submitted: Your transaction was submitted to the sequencer.
- Pending User Transaction: Your transaction has been decrypted but has not been included yet.
- Shielded Inclusion: Your transaction has been decrypted and included by the sequencer is now visible on Gnosisscan.
- Unshielded Inclusion: Your transaction was resent by the inclusion service, temporarily unshielded, before being fully included.
- Invalid: Your transaction is invalid.
- Cannot be decrypted: Your transaction cannot be decrypted.
- Not included: Your transaction couldn't be included.
The Technology Behind the Explorer
The Shutter Explorer is open source and constructed using a modern and scalable technology stack to manage the complexity and volume of data needed for real-time insights.
The Explorer is created using React with Typescript, a robust and scalable framework ensuring performance and maintainability. It utilizes Material UI (MUI) components to offer a clean and intuitive user experience.
The Explorer's backend is designed to securely query data from multiple sources, including the observer and Encrypting RPC. It uses JSON APIs to deliver real-time data to the front end, ensuring that the information displayed on the Explorer is always current. We plan to integrate GraphQL in future versions to enable more complex and flexible data querying.
Looking Ahead: Future Enhancements for the Explorer
The Shutter Explorer for Gnosis Chain is just the beginning. In the future, we will provide more information about MEV in general and additional integrations such as Snapshot and other partners. We plan to make future enhancements that include more advanced visualizations for tracking transaction lifecycles, slot progression, and real-time data on key generation.
Additionally, we intend to integrate more data sources and adopt advanced querying tools like GraphQL to provide an even richer experience for developers and advanced users.
Conclusion: A Major Step Toward Transparency and Security
The Shutter Explorer is a significant step forward in promoting transparency, security, and engagement within the Shutterized Gnosis Chain ecosystem. It provides real-time data on validator activity, Keyper participation, transaction lifecycles, and MEV protection, empowering users to control their network interactions. We encourage you to explore the Explorer, share your feedback, and join us in building a more secure and transparent decentralized network.
Follow us on X-Twitter, visit the Shutter Forum, and join our community on Shutter Discord to learn more about how Shutter works and stay updated on our progress.