Ethereum’s openness has sparked groundbreaking innovation. But that same openness comes with a downside: it leaves room for certain actors to manipulate how transactions are ordered or included in blocks. This is known as Maximal Extractable Value (MEV) - the profit that validators, sequencers, or searchers can earn by inserting, reordering, or excluding transactions. While MEV is not inherently harmful, some types can actually enhance market efficiency, while others may exploit users and erode trust in the system.
In this post, we’ll break down the two main types of MEV - the good (benign) and the bad (malicious). We’ll also show how Shutter’s encrypted mempool stops these harmful kinds while preserving the ones that help the system.
What Malicious MEV Looks Like
Malicious MEV is when someone uses insider access to profit by taking advantage of regular users. This typically happens when validators, sequencers, or searchers scan the public mempool (a kind of waiting area where unconfirmed transactions stay), spot pending transactions, and use that information to manipulate how transactions are ordered - extracting a profit at others’ expense without adding any value.
Here are the different forms:
- Front-running: This happens when someone sees your pending transaction in the public mempool and submits their own just before yours. For example, if you place a large buy order on a decentralized exchange (DEX), a front-runner can jump ahead, pushing the price up. Your trade goes through at a worse rate, and they profit from the price move you triggered.
- Sandwich Attacks: An attacker places one transaction before yours and one after. If you’re buying a token, they buy first to raise the price, let your trade go through, then sell immediately after at a profit. You lose value in the middle - they pocket the difference.
- Time-bandit Attacks: A validator revisits and reorganizes recent blocks to grab profitable MEV opportunities they initially overlooked. It’s extremely rare, but should it happen, it would significantly erode trust in the finality of transactions.
- Censorship for MEV: Validators or sequencers can create better conditions for their own MEV strategies by choosing to exclude or delay certain transactions. This behavior is particularly harmful in governance or DeFi applications.
What Benign MEV Looks Like
Not all MEV is harmful. Some strategies actually improve how DeFi systems work by helping markets stay efficient and stable. These approaches don’t exploit users - they support the system.
Here are the different forms:
- Arbitrage: This process involves identifying price differences for the same token across different platforms and executing trades to capitalize on them. It helps maintain consistent prices without requiring reordering of any transactions.
- Liquidations: On lending platforms, liquidators repay risky loans in exchange for collateral. This process helps maintain stability in lending systems and is a crucial part of their design.
- Back-running: This occurs when a transaction is placed immediately after a large trade to capitalize on small, predictable price shifts. Unlike front-running, it doesn’t interfere with or negatively impact the original transaction.
Encrypted Mempools: Reducing Harmful MEV, Preserving the Good
Shutter deploys encrypted mempools to protect users from malicious MEV while allowing for benign MEV that help markets function. These encrypted mempools are powered by threshold encryption and a decentralized network of nodes called Keypers.
How Shutter's Encrypted Mempool Works:
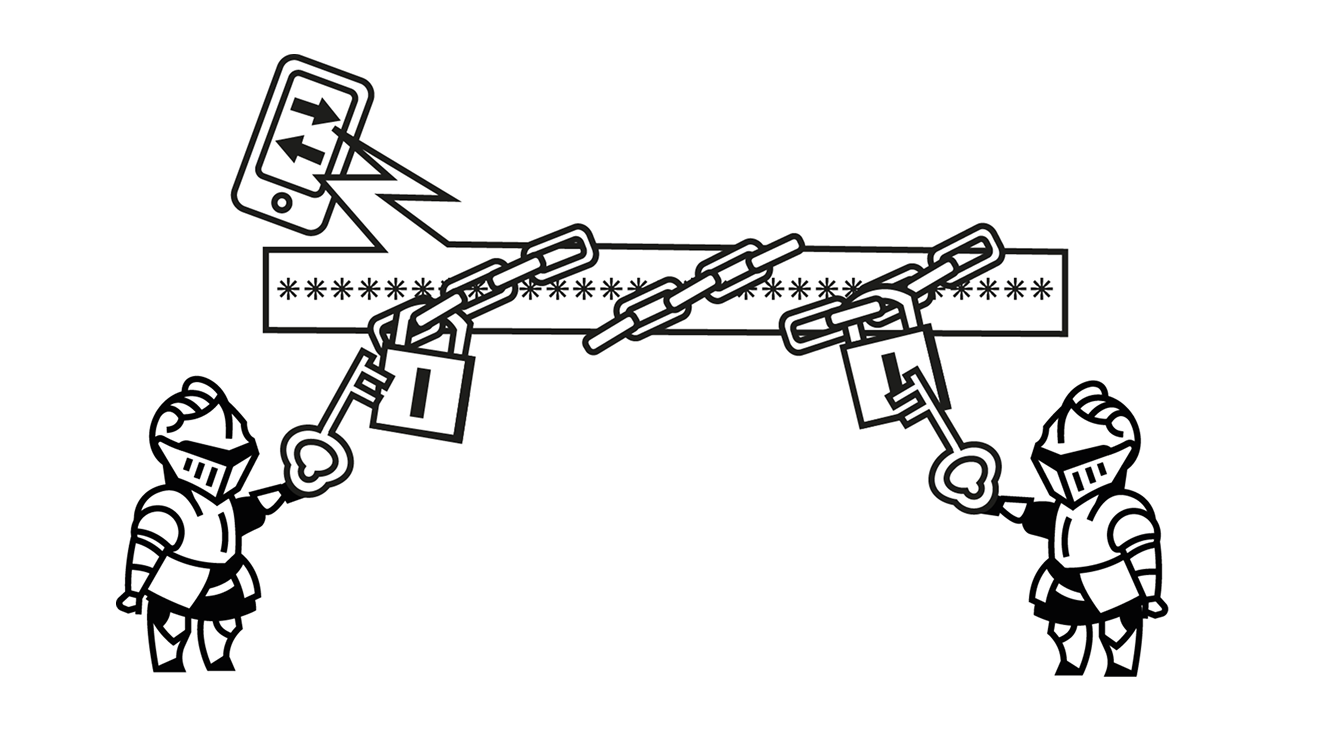
- Transaction Encryption: When users send a transaction, it is encrypted. This ensures that no one, including validators or sequencers, can read its contents.
- Submission and Holding: The encrypted transaction is submitted to the public mempool of the blockchain, where it awaits processing. Since the transaction is encrypted and unreadable, its contents are not visible.
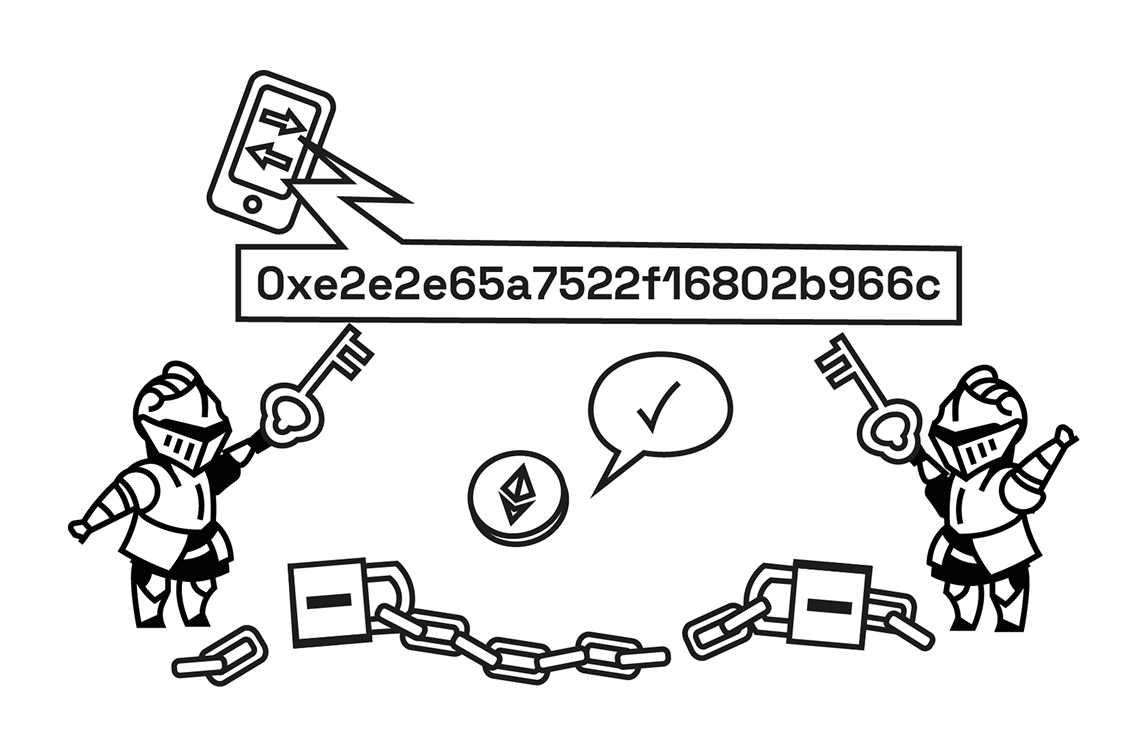
- Decryption and Execution: After the encrypted transaction(s) are included in a block, a group of Keypers collaborates to decrypt them. The transaction can only be decrypted and processed when a threshold number of Keypers reveal their parts of the decryption key.
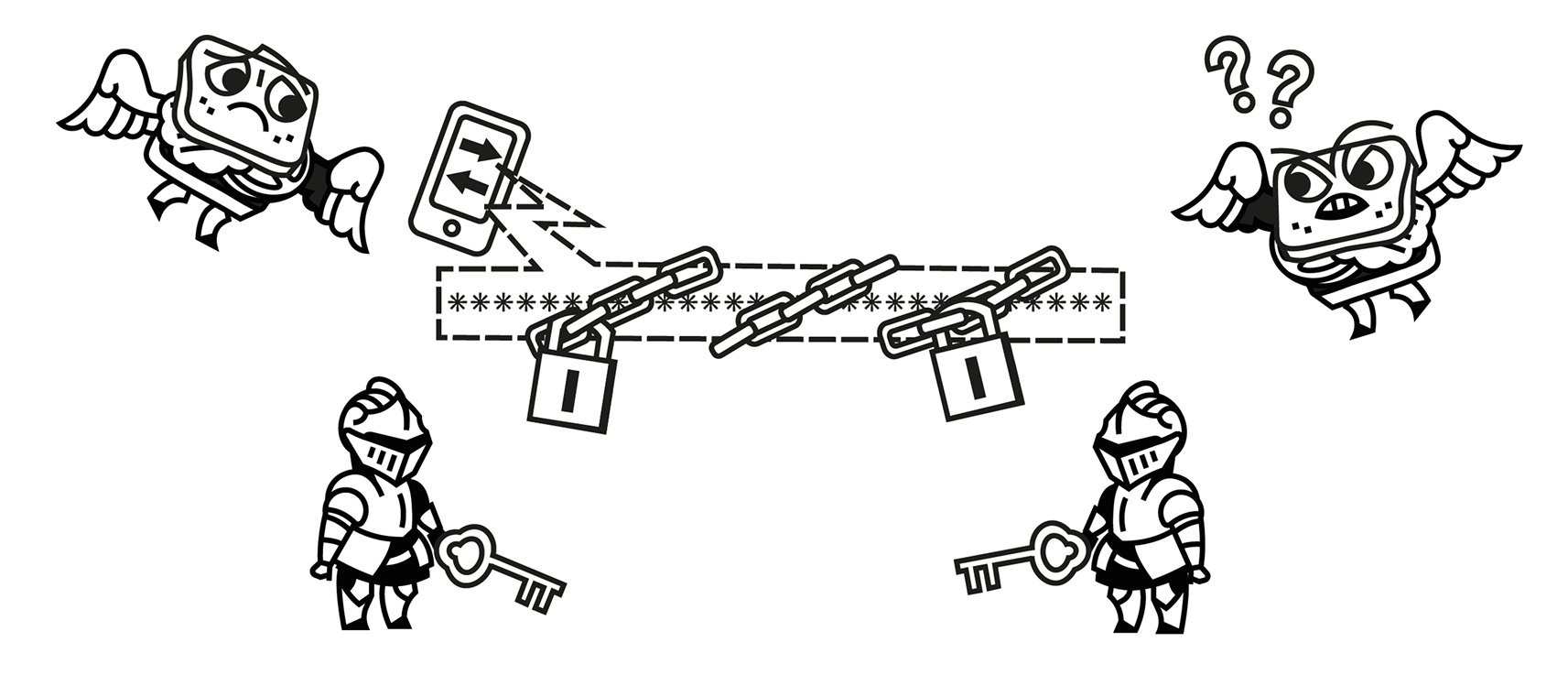
How Encrypted Mempools Dramatically Reduces Malicious MEV
- Privacy Until Execution: Since the contents of transactions remain hidden until they are included in a block, front-running, sandwich attacks, and censorship are dramatically reduced.
- Order Doesn’t Matter: Ordering becomes less relevant because the contents are encrypted. So then you can't extract profits from users from reordering (at least from front-running)
- Trustless Decryption: The system is structured so that no single entity can independently decrypt transactions. A majority of honest Keypers are required to reveal the data.
Preserving Good MEV
Shutter's encrypted mempools doesn’t stop all forms of MEV - just the malicious ones. Arbitrage, liquidations, and back-running remain possible after transactions are decrypted and included in a block. This balance makes Shutter's approach unique: it targets abusive behaviors while still allowing beneficial activities to continue.
This means:
- Honest traders can still improve market efficiency.
- Lending protocols can continue to depend on liquidators.
- Transaction reordering ceases only when it negatively impacts users, not when it benefits the system.
The Trade-offs: Costs vs. Benefits
While Shutter’s encrypted mempools have huge advantages, there are some trade-offs:
- Slightly Higher Fees: Encrypted transactions are larger, resulting in slightly higher costs due to increased data storage on the blockchain.
- Added Complexity: Requires extra infrastructure (Keypers) and secure key management.
- Minor Delays: There may be a slight delay in the visibility and execution of transactions, although they are still processed on time.
Despite these costs, encrypted mempools significantly boost trust and user protection, making these trade-offs worthwhile.
A Fairer Future for Ethereum
Shutter’s encrypted mempools offer a powerful way to improve Ethereum by reducing harmful MEV while preserving the benign MEV that keeps markets efficient. Beyond MEV protection, they also provide strong censorship resistance - keeping transactions private until block inclusion.
We’ve published a full proposal for how encrypted mempools could be implemented natively on Ethereum: Read the whitepaper
Curious what this looks like in action? Shutter is already live on Gnosis Chain: See the launch announcement
Encrypted Mempools aren't Just for Ethereum
Encrypted mempools can be integrated into most chains - whether on a Layer 1, a Layer 2 rollup, or even inside a DeFi protocol.
If you’re a core protocol developer - or simply want to see encrypted mempools on the chain you use most - we’d love to hear from you.







