Blog post was co-written with Samuel Huber, dTech.vision.
Building a mini app on Farcaster used to sound like rocket science. Now it’s as easy as opening ChatGPT, typing “make me a prediction market,” and watching your idea come to life. Generative AI turned what used to take a small team of engineers into a weekend project. Every day, new mini apps pop up on the feed like mushrooms after rain - some delightful, some dubious.
That’s both the beauty and the danger.
The same speed that makes it easy to ship an app also makes it easy to ship a scam. Anyone can spin up a “community prediction market,” “mystery pack,” or “onchain competition,” collect deposits, and vanish before the dust settles. And as Farcaster continues its breakout moment, the distinction between playful experimentation and quiet exploitation is blurring.
We’ve already seen a few early warning signs. Mini apps promising rewards for participation that quietly reroute funds, or games with “random” outcomes that are - well, not that random. A few were memes, others were full-on rug pulls. One, a so-called “social DeFi experiment,” turned out to be a front for siphoning user deposits through an obfuscated smart contract.
So, how do you tell the good from the bad?
In collaboration with dTech.vision, who’ve built and audited more production mini apps than anyone else in the space, we’re breaking down the three categories of Farcaster mini apps most likely to get exploited - and what to look for before you trust your wallet with them.
Because at the end of the day, a well-designed exploit looks exactly like a well-designed product.
The only difference is whether you can verify what’s happening under the hood.
Before We Start: What Mini Apps Can (and Should) Do Natively
Mini apps are web apps that run inside Farcaster clients, with an SDK to access native capabilities (auth, wallet, notifications, cast composer, etc.). They publish a manifest and embed metadata so your experience opens from the feed with one tap - no OAuth circus, no app store hop.
Useful primitives to watch for (and demand):
- Quick Auth / SIWF to sign in with Farcaster keys, not OAuth scopes. Data is already public, and writes happen via app keys. Less ceremony, fewer attack surfaces.
- Wallet access via EIP‑1193 (
getEthereumProvider/@farcaster/miniapp-wagmi-connector) and then typed EVM calls (we like viem for boring, reliable contract reads/writes). - SDK Actions like
compaseCast,sendToken,swapToken, andaddMiniApp, plus notifications—critical for growth loops and re‑engagement.
The most successful mini apps either optimize one KPI (transactions) or act as a top‑of‑funnel with slick sharing + referral economics baked in. Make the first action one click, add sound/visual “wow,” and let users brag directly from the mini app. You can even share fees with the original poster because you know who drove the session. That’s how mini apps compound.
The 3 Mini App Categories Most Likely to Get Exploited
1. Predictions or majority vote mini apps
Mini apps where you guess an outcome or pick a side are fun because they move fast and feel social. But these are also easy to game with if the right protections aren’t in place.
A couple of weeks ago the team behind the mini app game Ponder shared a user survey. And “collusion” showed up as a real concern.
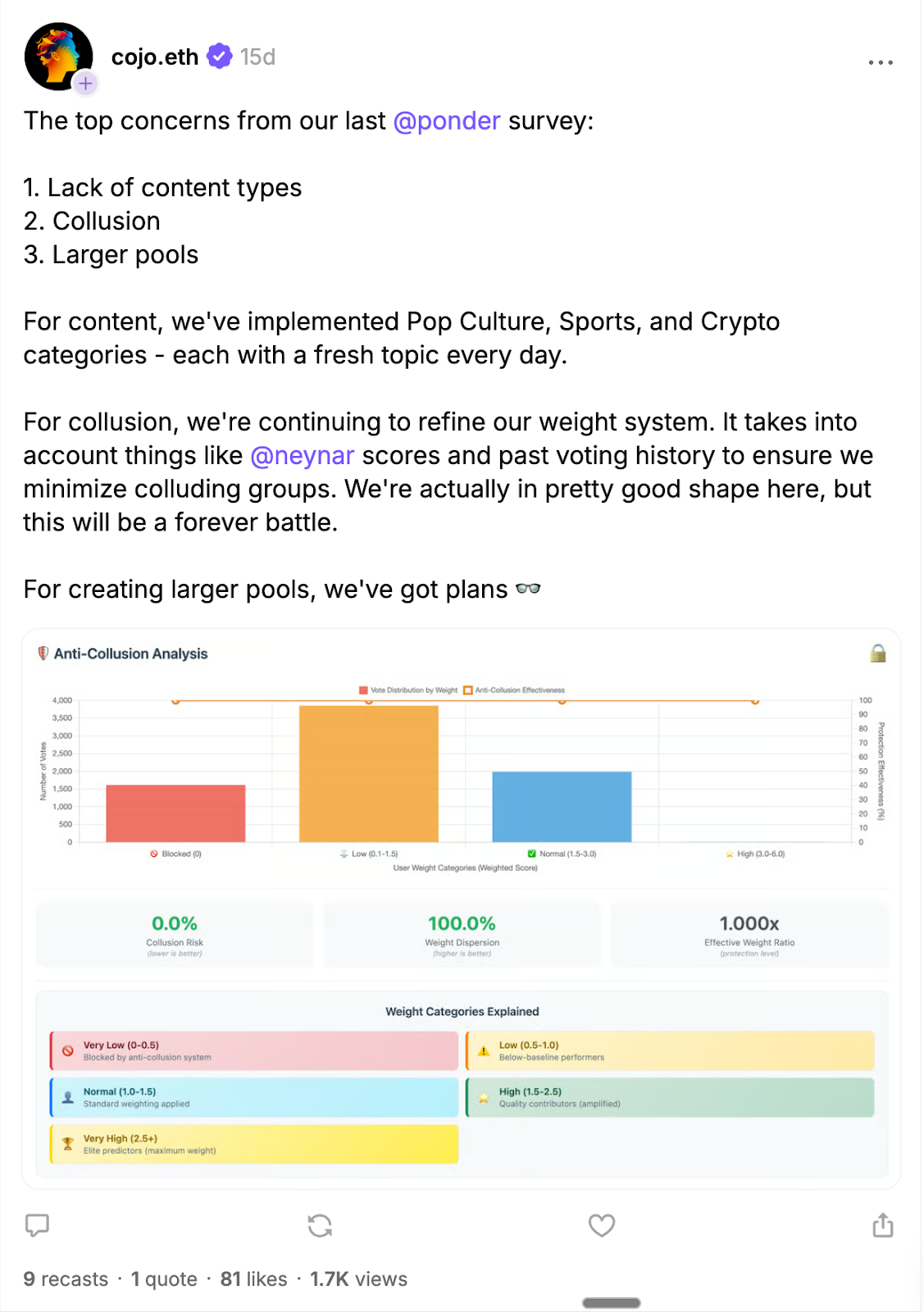
For those unfamiliar, Ponder is a prediction mini app on Farcaster where creators post questions, people vote what they think will be the most popular answer, and winners get paid based on the crowd result.
Collusion can take two main forms in this kind of mini app - one obvious, one hidden.
First, the obvious risk: If enough people or fake accounts pile on to one side, they can swing the result in their favor.
Second, the hidden risk: You have to trust that the people running the app are not peeking at votes before the reveal. You also have to trust they are not leaking early voting results to friends or to themselves so they can pick the winning side.
Ponder is just an example of this category. It is NOT a claim that Ponder is doing anything wrong. We are merely using its mechanism as an example. To their credit they asked users for feedback and are working to reduce collusion. However, the challenge is that without a way of verifying how results are protected through a trustless or at least trust-light design, you cannot fully know whether exploitation is happening.
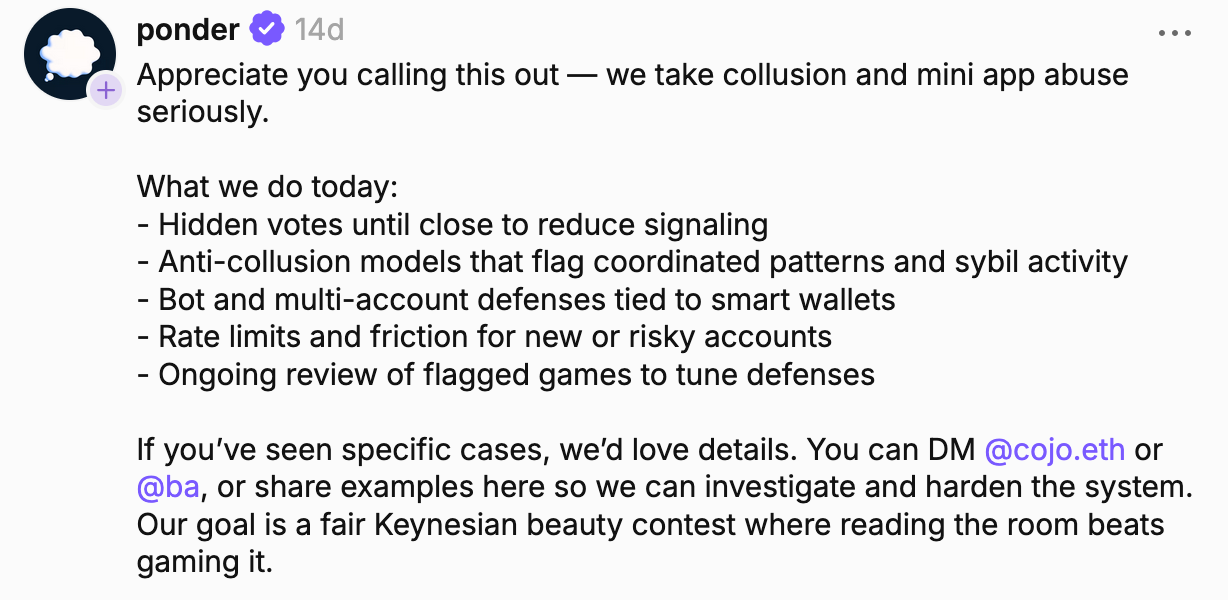
2. Head-to-head mini apps
Another major mini app category that's susceptible to exploitation are simultaneous move games. Think quizzes and quick challenges where two or more people act at the same time to answer correctly or do it better.
These games are only fair if everyone plays with the same information at the same moment. Rock, Paper, Scissors is the classic example. Poker and trivia fit too.
If one player can see a move or a card before the other, or can see the answers, then the game immediately becomes one-sided. The same idea applies to Farcaster mini apps that run these games.
The mini app Duel is a good reference point for the format. People across Farcaster compete in challenge-based games for money. Two of the games people can play are “Puzzleword” and “GeoSpot”.
Here’s the core issue. You have to trust that the people running the app are not peeking at players’ answers before the round ends and taking advantage of that information to win. You also have to trust that nobody else has early access to those answers.
Duel is just an example within this mini app category - and it's not a claim that Duel is taking advantage of users. But you should be very careful around mini app games that have some simultaneous move component. Especially when token rewards and payouts are involved, if there is no way to verify. Because exploitation is always on the table.
3. Mystery pack mini apps
The next at risk mini app category is mystery packs. These apps sell packs of NFTs or tokens, but you do not know what is inside at purchase time. You buy a pack, wait for the reveal, and see what you pulled. Think trading cards onchain. Most items are common. A few are higher value because of low serial numbers, special skins, one-of-a-kind pieces, or higher token value. And these traits can be random, user-chosen, or some other method.
Rips and Vibe.market are popular examples of this format. Mentioning them here is to show the category, not to make a claim about how they operate.
The main risk is trait sniping. This is when someone can predict which purchases will uncover the higher value items or the reveal timing can be gamed. It becomes possible when the draw is predictable. Sometimes an outsider can do it. In other cases insiders do it.
Using these apps you are trusting two things. First, that the people running the app are not peeking at outcomes and reserving the best packs for themselves or friends. Second, that regular players cannot predict or peek at the best packs before reveal. If you cannot tell how those risks are handled, you are taking the operator’s word for it.
The Issue These Mini apps Share - And What Fixes Them
All three categories of mini apps could fail to be honest in the same way. They expose intent or outcomes too early. That lets people peek, leak, or steer results. Sometimes it's outsiders gaming the flow. Sometimes it's insiders with extra visibility.
The fix to this is straightforward. These mini apps should implement commit-reveal threshold encryption. Here is what that means in practice:
- Users' choices are locked and hidden the moment they are made. The games’ answers stay encrypted and out of reach for everyone. When the round ends or a clear rule is met, everything is revealed at the same time and results are transparent. This makes them transparent and offers a way to inspect is what drives honest results.
- It also respects decentralization. The responsibility of encrypting and decrypting information is split among multiple participants, known as Keypers. Instead of relying on a single entity for the decryption key, a certain number of Keypers must work together to unlock the data.
Shutter API is a plug-and-play solution that can be integrated into mini apps to provide this valuable commit-reveal threshold encryption.
How to Verify That a Mini App is Safe
This is a bit of a challenge because you are here to play and win, not audit code. Still, a quick check goes a long way.
- Search for the mini app’s creators. If there's no info, that could be a warning sign.
- See if there’s a way to verify prior games results. If there’s no way to verify, that's an issue.
- Look for badges showing protection and audits by reputable organizations. Note: the purple Farcaster Pro badge is purchasable freely for anyone and not a sign of potential reputation!
If you’re still in doubt about a mini app that might post a risk. Ping us a message on Farcaster: dTech.vision (@samuellhuber.eth) and Shutter (@shutter). And we'll take a look!
Why This All Fits Mini Apps So Well
Mini apps collapse friction: instant auth, wallet in context, zero‑install. That’s why dTech’s clients either use them as top‑of‑funnel (capture, notify, DM, retain) or as the fastest path to a transaction (fewest clicks, share the wow). It’s also why bad actors like them. Cryptography (commit‑reveal + threshold) levels the playing field without asking users to become auditors.
Under the hood, the Farcaster SDK gives you the primitives (auth, wallet, actions, notifications), the manifest + embeds make your app discoverable in feeds, and the open nature of Farcaster means you don’t need OAuth permission dances to read public data. Keep writes cryptographically scoped with app keys, and you’ve got a tight, verifiable stack.
Harden Your Mini App Against Exploitation
If you have a mini app in one of the three categories we mentioned above, ping us a message on Farcaster. We can review your vulnerabilities and assess whether your mini app could benefit from commit-reveal threshold encryption.
- Shutter (@shutter)
- dTech.vision (@samuellhuber.eth)