We are thrilled to introduce Shutter API, a powerful and user-friendly threshold encryption service that offers distributed key management without depending on hardware-based trust assumptions. Shutter API broadens the opportunities for privacy-focused applications across various sectors, including gaming, governance, and finance. It enables seamless commit-reveal workflows, encrypted time locks, and improved transaction privacy.
Unlike the protocol-level encrypted mempool solution implemented on Gnosis Chain and which we have released as an OP Stack testnet, which remains a key priority, the Shutter API concentrates on the application layer. It makes threshold encryption accessible to any dApp developer. The Shutter API offers a flexible and lightweight method to integrate cryptographic fairness and confidentiality into Web3 applications, eliminating the need for in-depth cryptographic expertise.
The Shutter API is now live and already powers several early applications developed in-house. Over the past few weeks, we have been collaborating with developers to explore new use cases, and we are excited to see what comes next. Additionally, Shielded Voting on Snapshot will soon be migrated to the Shutter API, introducing threshold encryption for decentralized governance at scale.
Encryption Is the Key to Ethereum's Future and Fair Markets
Privacy isn't just an idealistic vision; it's a fundamental requirement for real-world applications. In many cases and increasingly so, information itself is money, and failing to protect it can lead to a loss of value even before it can be utilized. Traders, for instance, depend on having exclusive insights into the market. If this information gets revealed before they have a chance to act on it, its value diminishes immediately. This highlights the importance of temporary privacy and the critical role of encryption in securing financial transactions, auctions, and private business dealings. Shutter’s encrypted mempool offers this level of protection at the protocol level, ensuring fairer trading environments by preventing transaction front-running and information leaks.
Privacy is not only a concern for financial markets; it's also a significant barrier preventing Ethereum from achieving mainstream adoption for real-world applications. People are understandably hesitant to have their personal banking history, salaries, or private transactions fully visible on the blockchain. Additionally, businesses cannot function effectively if every strategic decision or contract negotiation is permanently exposed. This is why ensuring privacy on Ethereum is essential for reaching mass adoption.
In the long-term vision of a fully private blockchain future, Fully Homomorphic Encryption (FHE) emerges as a leading candidate. This technology allows computations to be performed on encrypted data without ever revealing the underlying information. However, FHE still requires secure key management, which is where Shutter comes in.
Encryption serves as humanity's last line of defense against malicious artificial intelligence and powerful computing technologies. Threshold key management ensures that this encryption remains trustless and resilient. The Shutter API enables developers to integrate this level of cryptographic security today, bridging the gap between Ethereum's transparent nature and the privacy demands of real-world applications.
Information Asymmetries Are Everywhere
Blockchain technology was meant to eliminate trust dependencies, but in reality, many dApps still suffer from hidden trust assumptions and information asymmetry. These issues allow privileged actors—whether it's validators, game operators, or auction hosts—to gain an unfair advantage over regular users.
In DeFi, traders lose billions to MEV attacks because their transactions are visible before execution. In DAO governance, early voters can influence the outcome of a proposal simply because their votes are publicly visible before the vote ends. In auctions, bidders may believe they're submitting a sealed bid, but in reality, the auction operator can see and potentially manipulate those bids before finalization.
The issues we face arise from one central problem: a lack of programmable privacy. For Web3 applications to offer genuine fairness, they must have a cryptographic method to regulate when information is disclosed. This ensures that no one can access privileged data prematurely, before the appropriate time.
Shutter API: Imagine a Sealed Envelope with a Stamp
The Shutter API offers developers a straightforward method to incorporate threshold encryption into their applications. It functions like a sealed envelope: a user commits to an action—whether it's making a bid, casting a vote, or taking a turn in a game—and then encrypts that action before submitting it, cryptographically "stamping" the envelope. This encrypted data remains completely unreadable until a specified time or condition is fulfilled. At that moment, the envelope is opened in a verifiable way.
Unlike centralized encryption services, the Shutter API does not depend on a single trusted entity to handle encryption or decryption. Instead, it offers access to a distributed threshold encryption network powered by Keypers—an independent group of node operators who work together to generate encryption keys. These keys are released only when specific predefined conditions are met.
Why We Need Cryptographic Fairness
Privacy is not merely a feature; it is essential to the functioning of society. In the digital world, information is power, and control over that information shapes outcomes. Without privacy, businesses, institutions, and individuals are at a disadvantage. The ability to selectively disclose information at the appropriate time is vital in competitive fields such as finance, governance, and gaming.
For Web3 to reach its full potential, it must address the information asymmetries that currently affect many blockchain applications. Right now, Ethereum lacks built-in privacy, making it unsuitable for a variety of real-world use cases.
The Role of Shutter and Shutter API
Shutter provides distributed threshold encryption as a service through Keypers, a network of independent node operators, ensuring privacy without a single trusted entity. The Shutter API allows dApp developers to easily integrate this encryption with simple API calls. While the protocol is distributed, the API acts as a centralized access layer, simplifying integration and making privacy and fairness easy to achieve for any dApp.
For Web3 to progress beyond its current limitations, commit-reveal encryption must become a standard feature. With Shutter API, dApps can eliminate hidden trust assumptions, prevent information leaks, and create fairer ecosystems for their users—all without the need for specialized cryptographic expertise.
Shutter API Use Cases
Integrating the Shutter API allows developers to improve existing applications and create new Web3 use cases that were previously impractical due to transparency issues.
Governance & Voting
Many DAOs currently use public voting, which allows early voters to influence the votes of those who come later. The Shutter API introduces Shielded Voting, ensuring that all votes are encrypted until the voting period concludes, promoting a fair and coercion-resistant process.
Sealed-Bid Auctions
Shutter API guarantees that bids remain confidential until the auction concludes. This prevents The Free Option Problem, in which bidders could submit multiple bids, observe others' bids, and then withdraw or modify their offers accordingly.
Fair On-Chain Gaming
Strategy games, including turn-based titles like Daoplomacy (a decentralized autonomous organization version of Diplomacy) and classic mechanics such as Rock, Paper, Scissors, rely on secrecy to ensure fair play. Without proper encryption, players or game operators could gain an unfair advantage by accessing hidden moves before they are revealed.
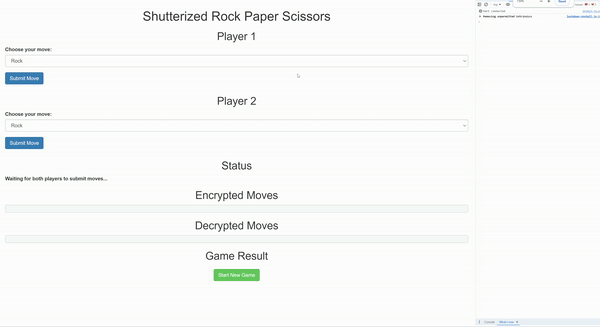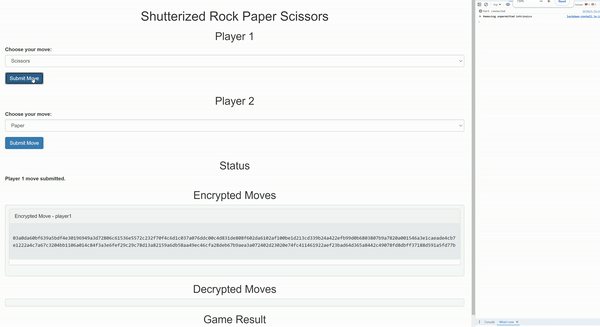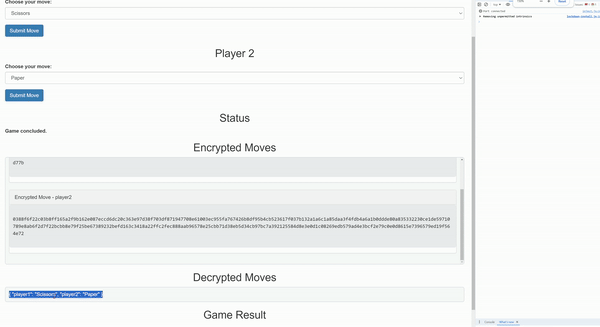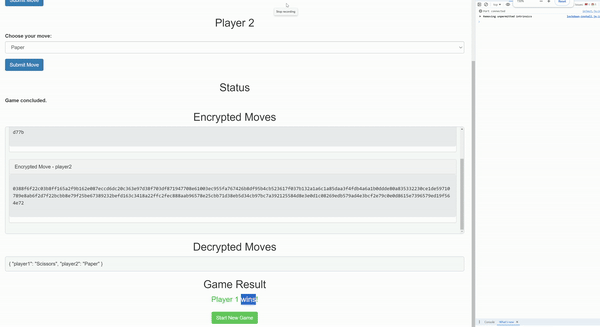
Werewolf and mafia-style games, where players have hidden roles and take secret actions, can significantly benefit from encrypted commitments. With the Shutter API, a player’s role and nighttime actions remain completely private until the game logic determines it’s time to reveal them. This prevents unfair peeking and ensures an authentic hidden-role experience.
The Shutter API ensures that all moves remain encrypted until they are simultaneously revealed. This guarantees that no player can respond to an opponent's decision before making their own choice. This feature is particularly useful in games like poker, where the Shutter API can enforce mandatory card reveals at the appropriate moments. This prevents players from withholding information or selectively showing their hands in order to manipulate the outcomes of the game.
Parimutuel Betting & Prediction Markets
By encrypting bets until a designated time, the Shutter API prevents manipulation during the late stages of sports pools, prediction markets, and DeFi options trading.
Smart Account Access to Encryption
Smart accounts bring enhanced usability and automation to Web3, but they currently lack the ability to access encrypted information. While Externally Owned Accounts (EOAs) can decrypt data today, smart accounts do not have the same capability. This limitation restricts the potential for private interactions, such as encrypted file storage, secure messaging, and controlled data access in decentralized applications.
Shutter API makes it possible for developers to build decentralized access control solutions for smart accounts by enabling them to interact with encrypted data. By associating a Shutter key with a smart contract, developers can create workflows where encrypted information remains hidden until a predefined condition is met, at which point a decryption key is released to a specific user.
For example, in a Fileverse-integrated smart account, encrypted documents could remain unreadable until an event within the smart contract grants access to a designated user. This ensures that access control is decentralized, automated, and verifiable.
Time-Locked Gifts & Payments
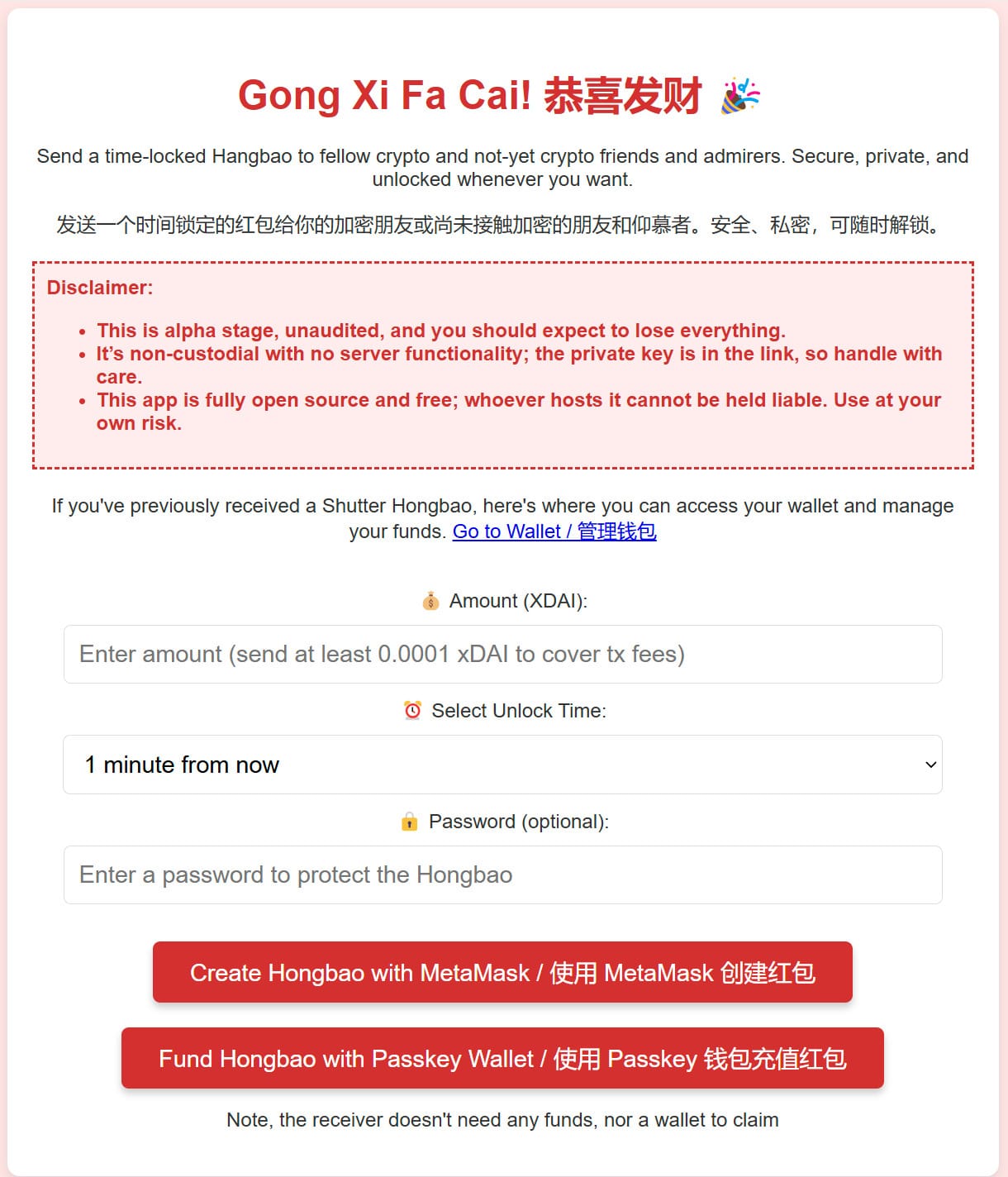
The Shutter API enables the locking of funds, NFTs, or encrypted messages until a specified time or event occurs. This feature allows for delayed transfers, inheritance smart contracts, and secret NFT reveals, ensuring that assets remain inaccessible until the designated conditions are fulfilled.
One example of this in practice is Shutter Hongbao, a decentralized gifting application that enables users to send time-locked red envelopes (hongbao) containing tokens or messages. Through the Shutter API, these gifts remain encrypted and can only be unlocked at a specified time, which preserves the element of surprise while ensuring fair and secure distribution.
How Does It Work?
Shutter API provides developers with an easy-to-use framework for encrypting and decrypting data based on predefined conditions. Integration requires just four simple API calls:
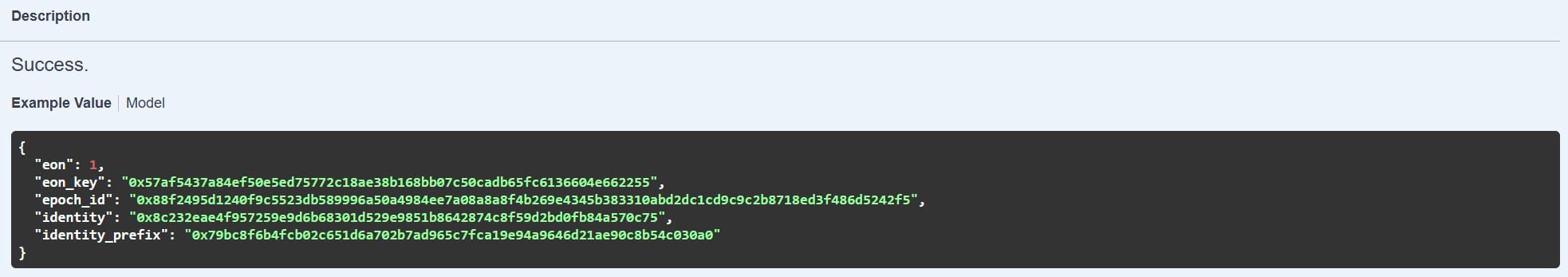
1) Register an Identity – Developers register a decryption trigger (such as a timestamp) using the API.
/register_identity
curl -X POST https://<API_BASE_URL>/register_identity \
-H "Content-Type: application/json" \
-d '{
"decryptionTimestamp": 1735044061,
"identityPrefix": "0x79bc8f6b4fcb02c651d6a702b7ad965c7fca19e94a9646d21ae90c8b54c030a0"
}'Example API Request
2) Encrypt Data – Retrieve encryption data and encrypt the commitment locally using the Shutter SDK.
/get_data_for_encryption
curl -X GET "https://<API_BASE_URL>/get_data_for_encryption?address=0xb9C303443c9af84777e60D5C987AbF0c43844918&identityPrefix=0x79bc8f6b4fcb02c651d6a702b7ad965c7fca19e94a9646d21ae90c8b54c030a0"Example API Request (Retrieve Encryption Data)
3) Submit Transaction – Execute the action, whether it's a game move, a bid, or a governance vote.
/get_decryption_key
curl -X GET "https://<API_BASE_URL>/get_decryption_key?identity=0x8c232eae4f957259e9d6b68301d529e9851b8642874c8f59d2bd0fb84a570c75"Example Request
4) Decrypt at the Right Time – Once the predefined condition is met, retrieve the decryption key and reveal the result.
/decrypt_commitment
curl -X GET "https://<API_BASE_URL>/decrypt_commitment?identity=0x8c232eae4f957259e9d6b68301d529e9851b8642874c8f59d2bd0fb84a570c75&encryptedCommitment=0x03b5685a460a95ba628e04b24155d6722f7c4e376a1627f714a4ae9cecd2982e005eff12ac8150b8842c29f8d5eaf4d0da0b626f762b4826d779d8969b577acb28df96cab026aa57c00cd74b07ca51e8c0c1a59933e29a728311900ebfc26c6804260914c96cb10dbd6d2ed3f6cb77788a74b5aae5f4ce6f40be53310a0524d42d5a6f03b5c1517ec097553733e228276fcdfc4b569f7ef4311a461d68819d634c"Example Request
Encryption Flow
- Setup – The user registers an identity on-chain with a decryption timestamp in the future. Shutter API can optionally cover the transaction fees.
- Encrypt – The user retrieves encryption data (the key) via the API or encrypts their data locally using the Shutter SDK. This encrypted commitment (e.g., a bid, vote, or game move) is submitted and recorded either on-chain or off-chain.
- Wait for Decryption Time – The encrypted commitment remains sealed until the predefined timestamp is reached.
- Decrypt – Once the decryption time has passed, the user either retrieves the decryption key via the API or decrypts the data locally with the Shutter SDK.
Why This Matters for Developers
The Shutter API streamlines the integration of threshold encryption for dApps, requiring no advanced cryptographic knowledge. It provides a self-service, permissionless solution that boosts fairness, privacy, and security.
Developers can easily add features like commit-reveal mechanisms, time-lock encryption, and other privacy-preserving tools.
Key Benefits
- Simple & Accessible – No need for cryptographic knowledge; the API and SDK handle everything.
- Trust-Minimized – Users don't have to trust a central entity; encryption keys are managed by a decentralized Keyper network.
- Automated & Tamper-Proof – Decryption happens only at predefined times or conditions, preventing manipulation.
- Versatile & Scalable – Works across gaming, governance, DeFi, NFT minting, and more.
- Proven & Reliable – Already securing Gnosis Chain and protecting 600+ DAOs on Snapshot.
With Shutter API, developers can build fairer, trust-minimized dApps—without the complexity.
Disclaimer
This software is in its early stages of development. Users are strongly advised to exercise caution and not entrust any assets or sensitive information of high value to this API until further maturity and decentralization are achieved.
Please note that all threshold cryptography systems and multi-party computation (MPC) frameworks inherently rely on a threshold trust assumption. While the Shutter API currently utilizes a decentralized set of Keypers, the network is still small and not fully decentralized at this time. We expect additional Keypers to join and enhance the network's resilience soon.
This project is released as open source and provided "as is" without any warranties, express or implied. The developers and contributors assume no liability for any issues, losses, or damages arising from the use or misuse of this API. Use at your own risk.
Get Started
Shutter API is live and ready for integration. Developers can get started by checking out the Shutter API documentation:
- Shutter API Documentation for dApp Developers.
- Quick Start Guide to Shutter API.
- How Shutter API Works.
This is just the beginning. We at brainbot and third-party developers are already creating new applications that utilize the Shutter API's encryption features, which will be coming soon. Stay tuned for a livestream tomorrow, where we will showcase these integrations, demonstrate real-world use cases, and discuss how encryption opens up new possibilities for Web3.
To explore more about how Shutter API is transforming Web3 privacy and fairness, visit docs.shutter.network.